HPE MSA - DISCERNING STORAGE ALLOCATION
10/01/21 - storage,msa,san,kb
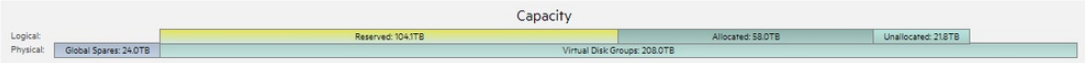
On the main/home screen, right in the middle is a bar which shows overall system Capacity. The top bar is your Logical capacity, and your bottom bar is the Physical capacity.
Simply put, your Physical capacity related directly to how many and what type of drives you have physically installed. If you put all of the disks in a single pool (pools can have multiple groups), then it'll be one single spot for all of your data. If you were doing a performance/archive (gold/silver) setup, you would not have a single disk pool.
Continue Reading -->REPAIRING WITH MDADM
09/01/2021 - mdadm,linux,kb,storage
When adding a new – or replacing an old – drive, sometimes you need to verify what the dev is inside of Linux.
# lsblk
Will give you a breakdown of how each block device is used (or, not). In the example to the right, you can see that /dev/sdg is empty. Before we go about adding it, let’s double-check our array
Continue Reading -->SSDs on RAID
12/12/20 - storage,kb
RAID arrays have been the foundation of storage systems since the 90’s, ranging from Small businesses to Enterprise environments. Originating from Berkeley in the 80’s, the concept of a RAID allowed to create storage redundancy and striping across multiple disks to allow storage from a single pool, instead of organizing between multiple separate volumes. Often times, creating an array with multiple inexpensive disks will outperform a single, larger disk in a large number of factors.
Not always expressly mentioned, another benefit of an array is an increase of read (and sometimes, write) speeds. Couple this with a larger single volume, and redundancy to protect against physical disk failure, and a RAID is an easy decision.
Continue Reading -->SOPHOS XG V18 FIREWALL RULES & NAT POLICIES
11/29/20 - firewall,sophos,kb
In XG v18, NAT policies were split from Security(Firewall in XG) rules. You can, however, create a “linked” NAT rule, which will only trigger when traffic passes that specific Security rule. But this won’t be covering that method.
Instead, this will be covering how to setup Firewall/Security and NAT rules on a system which splits those rules. In many firewalls you will come across, Security and NAT rules are kept and created separately.
This also largely covers the theory of firewall rules and NAT policies. While it is sort of brand specific to Sophos XG’s, the concept works across the majority of major firewalls.
Continue Reading -->DFSR AUTHORITATIVE RESTORE
11/24/19 - activedirectory,windows,dfsr,kb,storage
Steps should be ran from the Autoritative DC (generally the PDC Emulator role), unless otherwise noted.
You can verify which server has the PDC Emulator role by running from an elevated command prompt:
DOMAIN RENAME
11/23/19 - activedirectory,windows,kb
Foreword:
- If AD Connect/DirSync is installed, and there is an active sync to Azure AD/Office 365, uninstall it.
- Take some notes of which OUs are actively being synced
- Make sure you have a backup of DNS/ADDS
- While this COULD be done from a DC, or a domain-joined server, it may be easier to do this from a domain-joined workstation – even one which is spun up only for this purpose.
- You will need some of the RSAT tools installed for ADDS, DNS, and GPM
- Wherever you choose to do this, this system will be referenced as the Control System from this point forward